Module 3 - Scanning & monitoring for insecure Kubernetes configurations
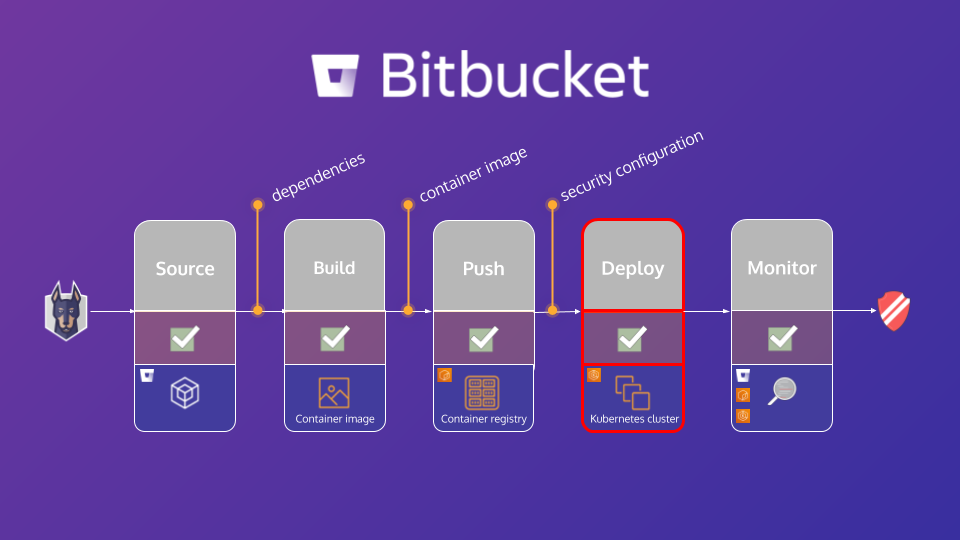
Configuration management shifting left1
Traditionally, developers have been responsible for just writing the code — someone else was responsible for quality. Yet another person was responsible for deploying it. And, another team was responsible for running it in production. But increasingly we’re seeing more and more responsibilities shift to the development teams, with specialists providing expert support and consultancy. We’ve seen software packaging move from a specialism in IT, to developers writing Dockerfiles. We’ve seen the rise of DevOps, “you build it, you run it” and development teams owning services in production. And we’re now also seeing configuration increasingly become a developer domain problem with the rise of infrastructure as code and tools like Terraform, Kubernetes and AWS CloudFormation.
Learning objective
In this module, you will learn how to secure your Kubernetes workloads. We wil cover the following topics:
- Overview of Snyk controller and its architecture
- Deploying your applications to Amazon EKS
- Adding Kubernetes workloads for scanning & monitoring
- Interpreting scan results and fixing discovered issues